Introduction
Just a few days ago, AWS unveiled a new type of VPC endpoint, aptly named the EC2 Instance Connect Endpoint. Prior to this, accessing resources within a VPC from the internet necessitated the use of an EC2 Bastion server and SSH. Even if we resorted to using the session manager through AWSCLI, we were left with no method to access an RDS instance in a private subnet from the internet.
However, with the introduction of this VPC endpoint, we might soon see a shift away from using EC2 Bastion servers to access RDS Instances in private subnets. This development is substantial, and I anticipate it will instigate substantial transformations in system architectures.
Now, let’s dive deeper into EC2 Instance Connect and its VPC endpoint to understand the potential impacts and the how-to’s of this newly launched feature.
What is EC2 Instance Connect?
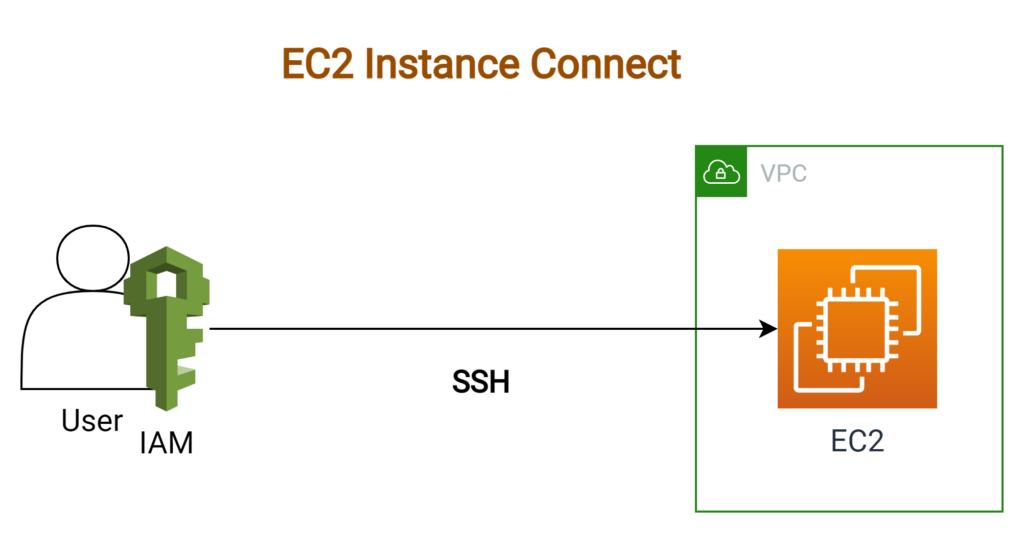
Launched back in 2019, AWS EC2 Instance Connect is a service that provides a secure and auditable method to connect to your EC2 instances. EC2 Instance Connect works by allowing you to use AWS Identity and Access Management (IAM) policies and principles to control SSH access to your instances, eliminating the need to share and manage SSH keys. This service provides a simple and secure connection method, significantly enhancing the ease-of-use and security of your EC2 operations.
However, despite its advantages, EC2 Instance Connect had its own set of limitations prior to the introduction of its VPC endpoint. Primarily, this was due to the fact that the process involved setting up additional infrastructures like an EC2 Bastion server or using the AWSCLI and Session Manager for connectivity, which increased the complexity of the entire process. Furthermore, there was no direct way to access an RDS instance located in a private subnet from the internet using EC2 Instance Connect, limiting its utility.
With the recent advent of the VPC endpoint for EC2 Instance Connect, you no longer need to navigate through these complexities. This launch has streamlined the entire process, making it significantly easier to manage and establish connections to resources within your VPC, thus enhancing the user experience.
How to Use VPC Endpoint of EC2 Instance Connect
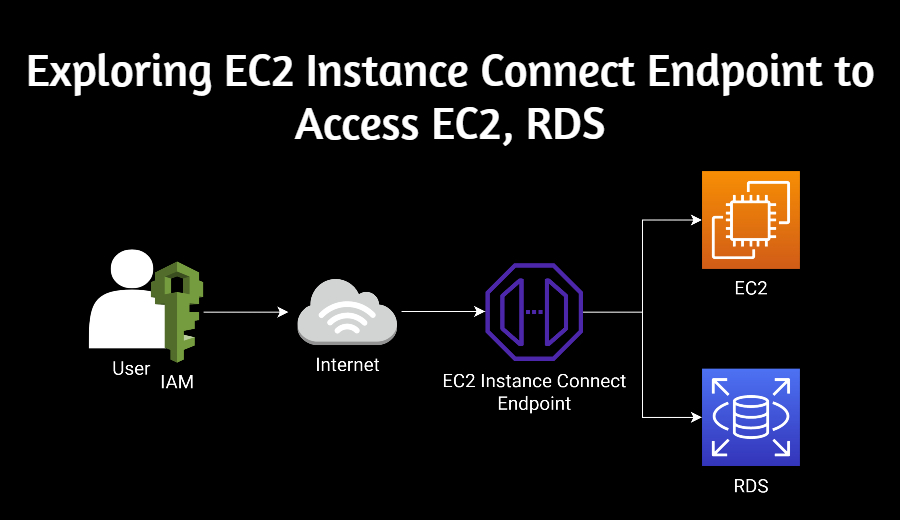
As we discussed, EC2 Instance Connect has introduced a unique VPC endpoint. It’s an enabling bridge between the internet and resources in your VPC. You can access this via the AWS console.
While AWS documentation provides a theoretical grounding, hands-on exploration of the console’s features provides a more practical understanding of this new service. So, don’t hesitate to dive in and experiment with this newly introduced VPC endpoint. Let’s delve deeper into its usage.
Prerequisites for Using EC2 Instance Connect VPC Endpoint
Before we get hands-on, it’s vital to ensure we have the necessary prerequisites set up:
- The OS of the instance you wish to connect should be Amazon Linux 2 2.0.20190618 or later, or Ubuntu 20.04 or later. If your instance doesn’t meet these requirements, you’ll need to install EC2 Instance Connect manually.
- Make sure you have AWS CLI Version 2 installed.
- Finally, you must have suitable permissions set up locally, such as IAM User or AssumeRole.
For comprehensive details, refer to the official AWS documentation
Once these prerequisites are in place, we can proceed to set up the EC2 Instance Connect VPC endpoint. The process is similar to establishing other VPC endpoints. Navigate to the VPC endpoint console, click the ‘Create VPC Endpoint’ button,
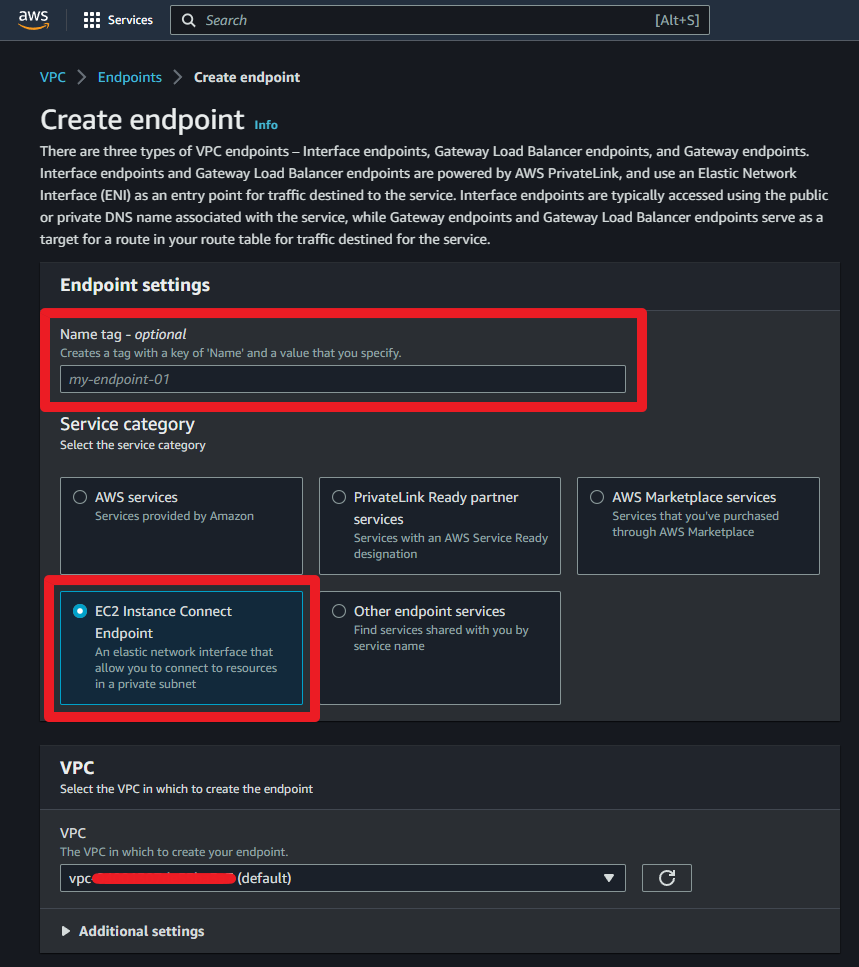
and fill in the necessary settings. With these steps completed, we’re ready to use EC2 Instance Connect to access EC2 and RDS instances.
Accessing EC2 Instance
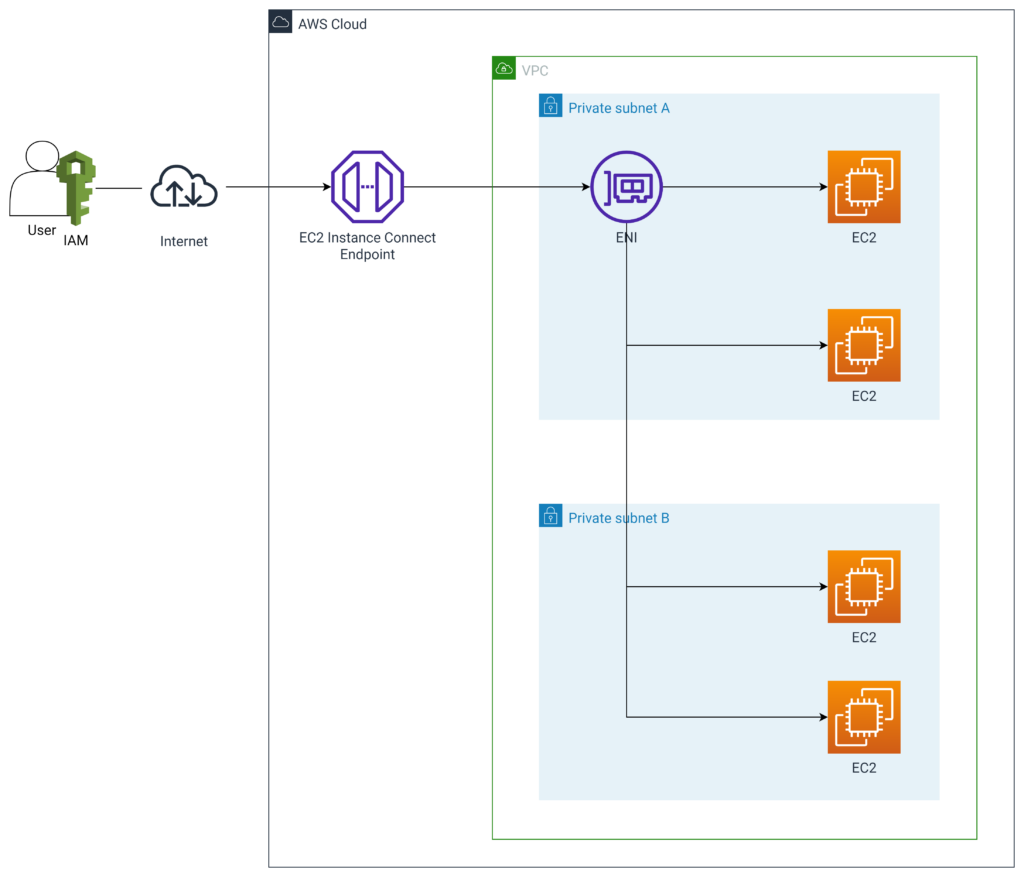
So, how do we access an EC2 instance using EC2 Instance Connect? There are two straightforward methods: using the AWS console and AWS CLI.
Firstly, you can access it directly through the AWS console. This process closely mirrors how one would connect to an EC2 instance via SSM in the AWS EC2 console. Navigate to the EC2 console, right-click on the corresponding EC2 instance, and select ‘Connect’. This action will open a terminal connected to your EC2 instance.
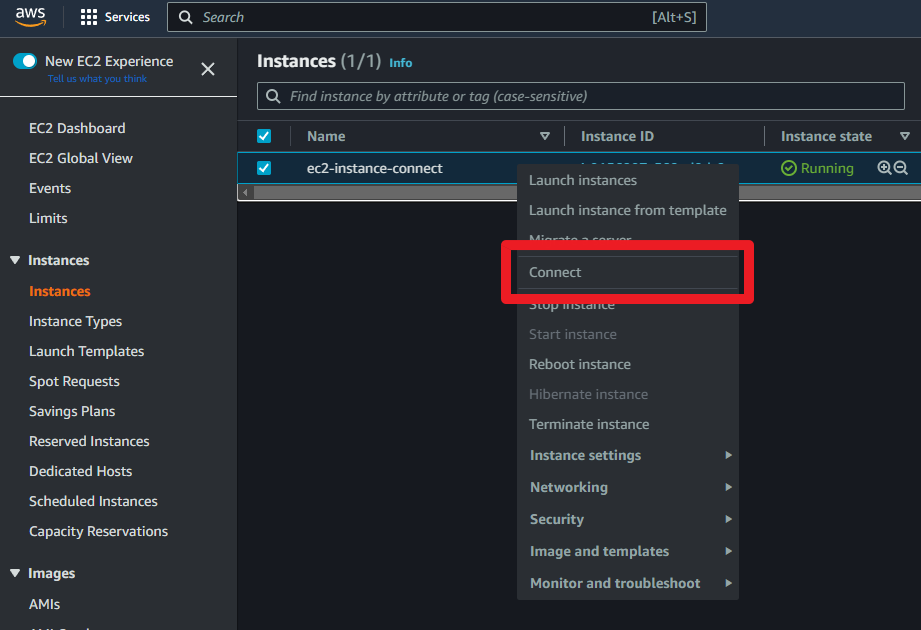
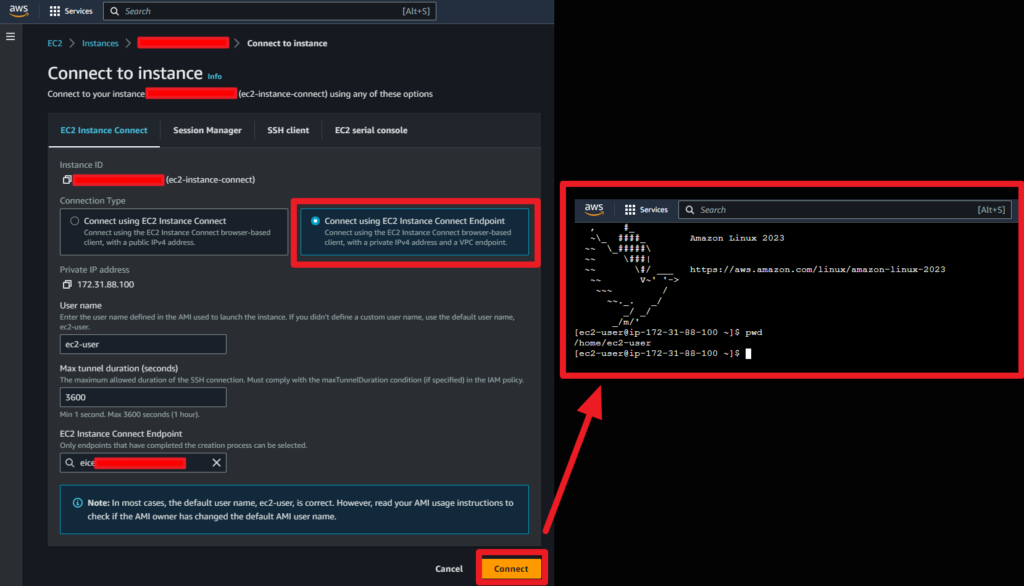
Secondly, you can utilize EC2 Instance Connect through AWS CLI. Run the following command in your local terminal, replacing ‘i-xxxxxxxxxxxx’ with your instance ID:
aws ec2-instance-connect ssh --instance-id i-xxxxxxxxxxxx --connection-type eice
If your AWS CLI doesn’t recognize this command, you might need to update it.
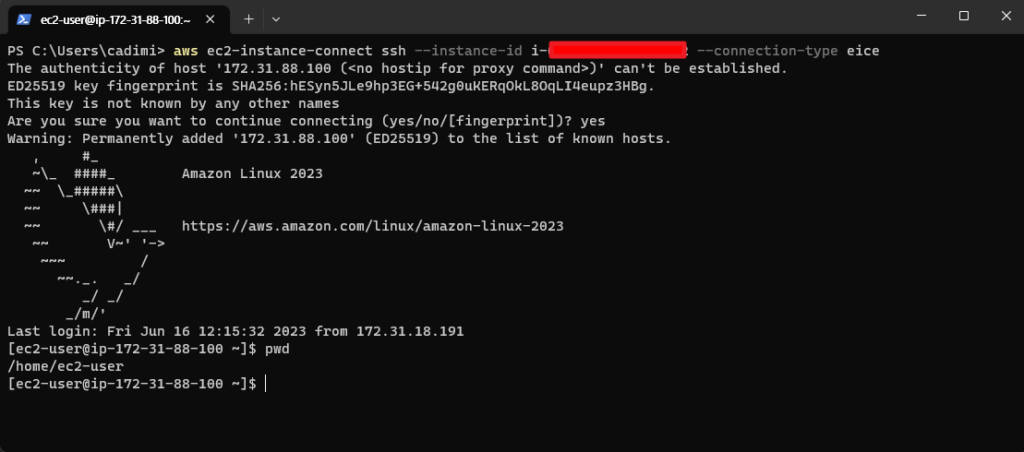
This single command is a handy tool. Internally, it combines the ‘aws ec2-instance-connect send-ssh-public-key‘ and ‘aws ec2-instance-connect open-tunnel‘ commands before establishing an SSH connection, thus streamlining the connection process.
In conclusion, EC2 Instance Connect offers a significantly smoother experience when it comes to accessing EC2 instances. Yet, it’s crucial to remember one key detail. If the maximum tunnel duration, or ‘max_tunnel_duration’, is exceeded, the WebSocket connection will be closed.
From my experience, while accessing from the management console, the process ended up hanging without any error message. This appears to indicate there’s no mechanism currently in place for extending the session duration. Therefore, should this period be exceeded, it becomes necessary to reconnect each time. Being aware of this can help avoid unexpected interruptions in your sessions and maintain a seamless operation.
Accessing RDS Instance
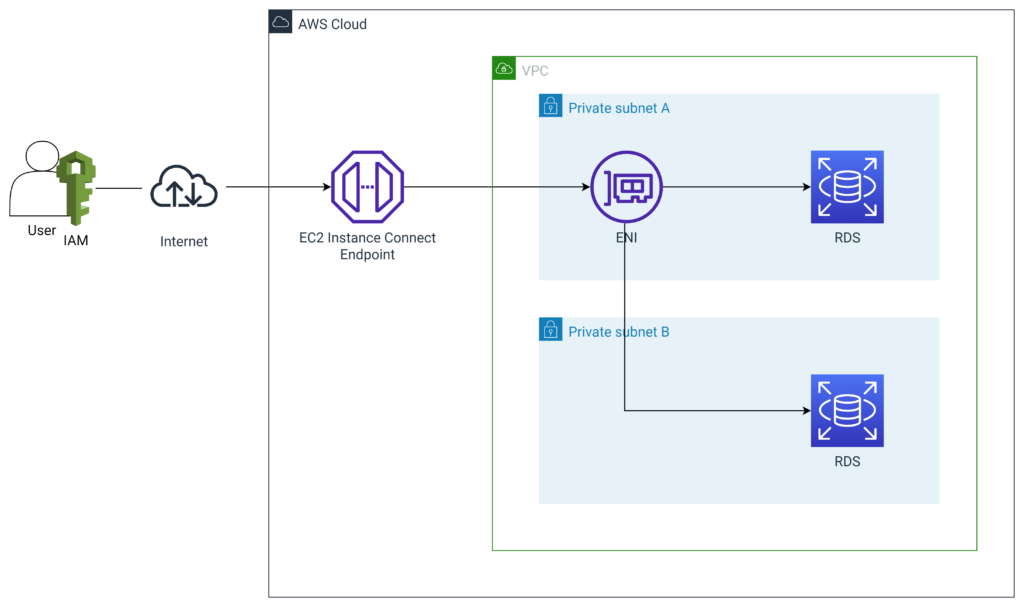
When it comes to accessing RDS instances, the process differs slightly from EC2. We must first open a WebSocket tunnel with the following command: aws ec2-instance-connect open-tunnel.
aws ec2-instance-connect open-tunnel --instance-connect-endpoint-id "VPC Endpoint ID"--private-ip-address "Private IP"--local-port "random port number to use locally" --remote-port "rds port number"
this requires four parameters:
- instance-connect-endpoint-id: the EC2 Instance Connect endpoint ID
- private-ip-address: the target private IP (in this case, it should be the private IP of the RDS)
- local-port: the port of the device we’re using
- remote-port: the access port of the RDS
Finding the remote port and local port is straightforward. However, the AWS RDS console doesn’t directly provide the private IP, only showing the Endpoint URL. Thankfully, we can obtain the private IP by using the ping command along with the RDS Endpoint URL.
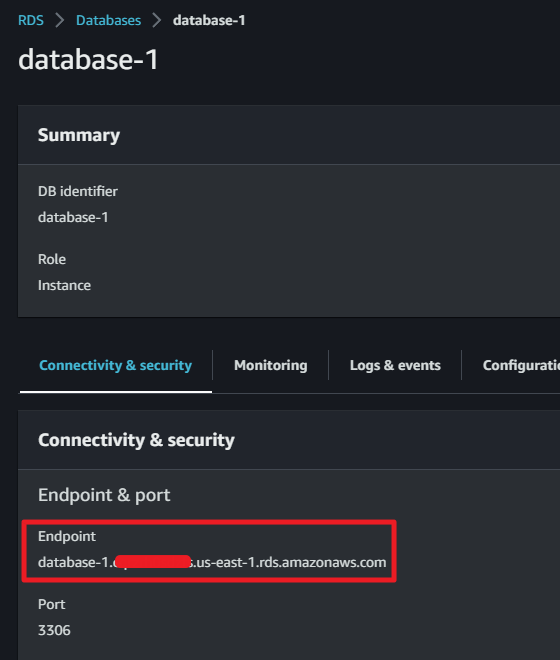
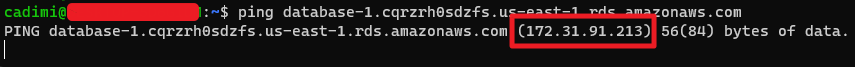
Once we’ve gathered all the necessary information, we can open the WebSocket tunnel. After opening the tunnel, we can access the RDS with the corresponding client (for this example, I used the MySQL client).
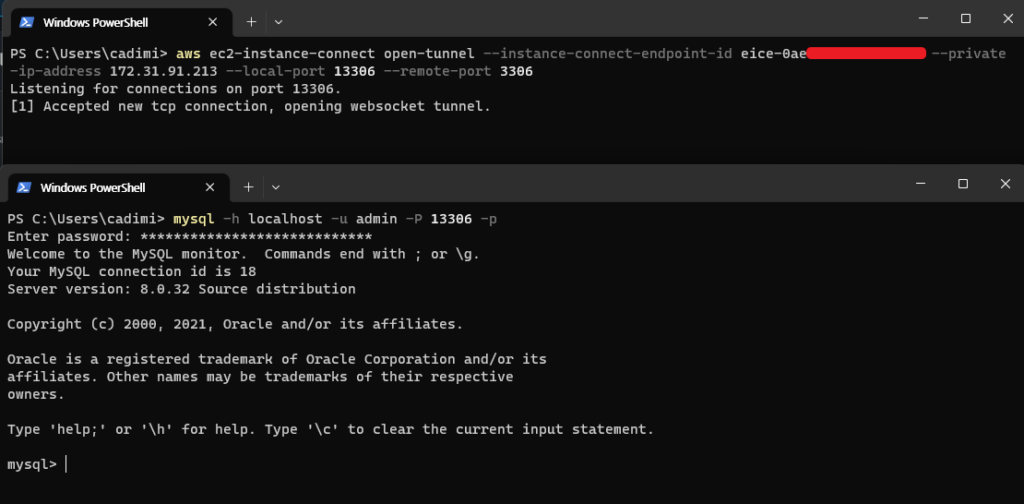
We can see it worked well. but remember, everything might not work as smoothly if the security group settings of the RDS instance do not allow inbound traffic from the VPC endpoint. It’s worth giving them a check to ensure no connection issues arise.
Comparing EC2 Bastion Server, EC2 Instance Connect with Its Endpoint, and Session Manager
Until the introduction of the EC2 Instance Connect VPC Endpoint, we were generally restricted to using the EC2 Bastion Server or AWS System Manager Session Manager based on the situation.
However, we now have another viable choice. Let’s compare these options:
| Feature | EC2 Instance Connect and VPC Endpoint of it | EC2 Bastion Server | AWS Systems Manager Session Manager |
|---|---|---|---|
| Purpose | Provides a secure way to connect to EC2 instances or RDS in a VPC without opening a port in your security group. | Provides a secure jump point for accessing other EC2 instances in your VPC. | Provides a secure way to connect to your EC2 instances using the AWS Management Console, the AWS CLI, or the AWS SDKs. |
| Accessible Resources | EC2 and other resources such as RDS | Any AWS resource | Primarily EC2 related resources |
| Security | Connections are encrypted using TLS. | Connections are encrypted using SSH. | Connections are encrypted using TLS. |
| Authentication | Uses your IAM credentials. | Uses your IAM credentials or a pre-shared key. | Uses your IAM credentials. |
| Cost | No additional cost (As of June 2023) | Requires an EC2 instance, which incurs costs including management. | No additional cost. |
| Management | Easy to manage. | Requires manual management. | Easy to manage. |
As seen above, there seem to be fewer reasons not to use EC2 Instance Connect and its endpoint. Currently free, it eliminates the additional costs associated with running and managing an EC2 Bastion Server.
Moreover, despite their similarities, it’s safe to say that EC2 Instance Connect and its VPC endpoint, in most cases, outperform the AWS Systems Manager Session Manager, especially when it comes to providing an access path to RDS.
Conclusion
In conclusion, we’ve explored the EC2 Instance Connect VPC endpoint and how it can be utilized. As with any technology, choosing the appropriate resources for your project requires careful consideration of various factors.
From my perspective, the advent of the EC2 Instance Connect VPC endpoint presents a compelling case to reevaluate the use of traditional EC2 Bastion servers. The ease of management, coupled with cost-effectiveness and enhanced security, all contribute to its rising appeal.
In closing, I’d like to emphasize the importance of selecting technologies based on the specific needs and requirements of each individual project. While the EC2 Instance Connect VPC Endpoint brings many promising features, it’s crucial to remain adaptable and flexible in our rapidly evolving technological landscape. Always weigh the pros and cons of each tool and make decisions that align with your project’s unique characteristics and goals.