What is Ansible?
Recently, Ansible has gained widespread recognition as the technology was adopted as the main focus in the RHCE certification process in 2022. Primarily, Ansible is a configuration management tool. To fully grasp Ansible, it’s important to first understand the concept of configuration management.
Configuration management is the practice of maintaining and controlling the state of systems, applications, and infrastructure components in a consistent and reliable manner. It’s essential because it ensures that all components within a system are functioning together seamlessly, reduces errors, and simplifies troubleshooting. For example, in a large organization with multiple servers, maintaining consistent software versions, security settings, and user access permissions is crucial for smooth operations. Configuration management tools automate this process, allowing administrators to efficiently manage complex environments.
Apart from Ansible, there are several other configuration management tools, such as Chef, Puppet, and SaltStack. If you’re familiar with AWS, AWS Systems Manager State Manager is another noteworthy configuration tool, as it helps engineers maintain and control AWS resources.
Although the main feature of Ansible is configuration management, it also offers other features like application deployment and infrastructure provisioning. However, many organizations choose Ansible solely for configuration management purposes due for various reasons.
Among the numerous configuration tools available, Ansible stands out for being actively developed as an open-source project and is widely adopted across diverse industries and departments.
What’s different between Ansible and Terraform?

Terraform is another popular tool in the DevOps space, but it differs from Ansible in its primary function. While Ansible is a configuration management tool, Terraform focuses on provisioning cloud infrastructure as code.
From a technical standpoint, Ansible excels at managing the state of individual system components, such as software installations, file configurations, and user permissions. It automates tasks using playbooks written in YAML, a human-readable data serialization language. Ansible achieves its goals through a push-based architecture, where changes are pushed to the target nodes from a central control machine.
On the other hand, Terraform is designed to manage the overall structure of cloud environments, including the creation, modification, and deletion of resources like virtual machines, storage, and networking components. It uses a declarative language called HashiCorp Configuration Language (HCL) to describe the desired end state of the infrastructure. Terraform employs a pull-based architecture, where it calculates the differences between the current and desired states and then makes the necessary changes.

Imagine a theater production. Configuration management tools are like the stage manager, ensuring all actors, props, and set pieces are in the right place and functioning correctly. On the other hand, cloud infrastructure provisioning tools like Terraform are like the set designers, creating and arranging the stage to meet the requirements of the production.
As such, these two tools have very different development ideas and goals to achieve.
Ansible’s Design Goals and Features
Ansible’s design goals and features focus on creating a tool that is efficient, secure, and easy to use for managing infrastructure and applications. The developers aimed to build a system that would cater to the needs of users while minimizing complexity. These design goals, evident in the core principles of Ansible, are complemented by a rich set of features that allow for effective provisioning, configuration management, orchestration, application deployment, and security compliance. Together, these goals and features form the foundation of Ansible’s robust and flexible capabilities.
Design Goals
- Minimal In Nature: Ansible strives to keep its core as simple as possible. This means that it avoids unnecessary features and complexities, making it easier for users to understand and maintain the system. The minimalistic design helps reduce the likelihood of errors and ensures that the tool remains lightweight and fast.
- Consistent: Consistency is key to Ansible’s design philosophy. It aims to provide a uniform experience across different platforms and environments, ensuring that users can easily apply their knowledge and skills to various situations. This consistency extends to aspects like configuration, module usage, and API interactions.
- Secure: Security is a top priority in Ansible’s design. By default, it uses Secure Shell (SSH) for communication between the control machine and the managed nodes. This provides strong encryption and authentication, ensuring the integrity and confidentiality of data transferred between the systems.
- Highly Reliable: Ansible is built to be highly reliable, so users can trust it to manage critical infrastructure components. It employs an idempotent approach to executing tasks, meaning that the desired state is only applied if it differs from the current state. This ensures that tasks can be run multiple times without causing unexpected changes or errors.
- Minimal learning required: Ansible’s design aims to minimize the learning curve for users. Its use of YAML for writing playbooks provides a human-readable and easy-to-understand format, while it is agentless architecture and modular design allow users to quickly grasp the concepts and start using the tool effectively.
Features
- Provisioning: With Ansible’s cloud modules, users can efficiently manage and provision infrastructure across numerous cloud providers, including AWS, Azure, and GCP. These modules facilitate creating, altering, and removing cloud resources, making Ansible a strong contender for automating infrastructure provisioning tasks.
- Configuration Management: Ansible shines in maintaining the desired state of systems through configuration management. Utilizing playbooks and modules, users can automate tasks like package installations, service management, and file modifications, ensuring a consistent and reproducible environment across their infrastructure.
- Orchestration: Ansible orchestrates tasks across groups of systems by coordinating multiple tasks simultaneously. Features such as inventory management, host targeting, and playbook task ordering empower Ansible to automate intricate, multi-tier application deployments and manage dependencies between tasks and systems.
- Application Deployment: Ansible simplifies deploying applications across different environments thanks to its role-based approach and support for custom modules. Users can develop reusable roles to define application configurations and dependencies, streamlining the deployment process while maintaining consistency across environments.
- Security and Compliance: Ansible’s built-in modules and features, like Ansible Vault for encrypting sensitive data, help ensure security and compliance throughout the infrastructure. Users can automate tasks related to security updates, system hardening, and policy enforcement, guaranteeing that systems adhere to the necessary security standards.
Ansible Architecture
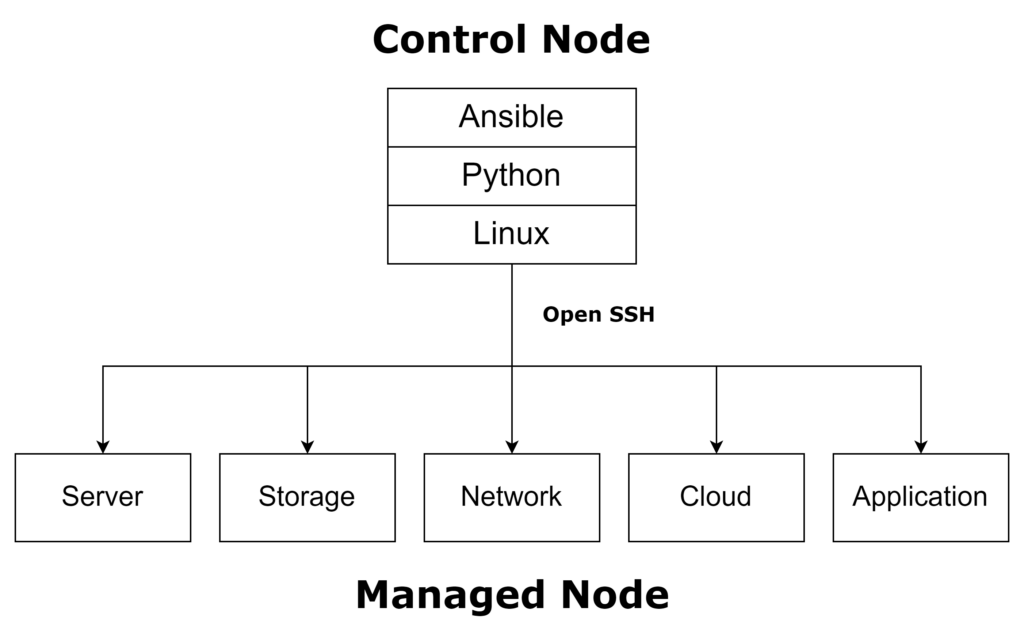
Ansible’s architecture is designed around a simple yet powerful structure. In this architecture, one control node (server) is responsible for managing multiple managed nodes (clients). Communication between the control node and the managed nodes is securely facilitated through SSH (Secure Shell), ensuring the integrity and confidentiality of the data being transferred. This straightforward architecture allows for efficient, secure, and scalable management of infrastructure components.
Control Node
The control node in Ansible’s architecture serves as the central point of management for the entire infrastructure. It is the system where Ansible is installed and from which playbooks and commands are executed. The control node communicates with managed nodes through SSH, pushing configuration changes and orchestrating tasks across the infrastructure.
Managed Node
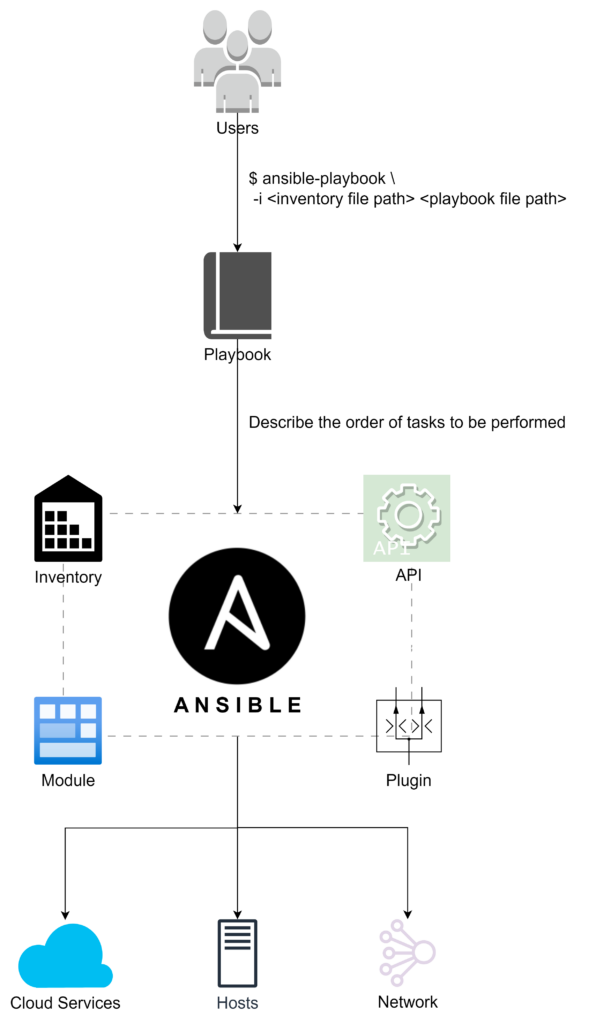
Managed nodes are the individual systems or devices that are managed and configured by the control node. They can be physical machines, virtual machines, or network devices. Ansible does not require any special software to be installed on the managed nodes, as it relies on SSH for communication. Key components of the managed node in Ansible’s architecture include:
- Inventory: The inventory is a list of managed nodes organized into groups. It provides a way to target specific systems or groups of systems for configuration tasks. The inventory can be defined in a static file or dynamically generated from various sources, such as cloud providers or configuration management databases (CMDBs).
- Playbook: A playbook is a YAML file that defines a set of tasks to be executed on the managed nodes. It outlines the desired state of the system and serves as the primary method of defining configuration management and orchestration tasks in Ansible. Playbooks can include variables, conditional statements, loops, and other constructs to enable complex configurations.
- Module: Modules are reusable, standalone scripts that perform specific tasks in Ansible. They can be used to manage system resources, such as files, packages, services, or network configurations. Ansible includes a large collection of built-in modules, and users can also create custom modules to meet their specific needs.
- API: Ansible’s API allows external systems and applications to interact with the control node, enabling tasks to be executed and managed programmatically. The API provides a way to integrate Ansible with other tools, such as monitoring systems, continuous integration/continuous deployment (CI/CD) pipelines, or custom web applications.
- Plugin: Plugins in Ansible are used to extend the tool’s functionality by adding features or modifying existing behaviors. They can be used to create custom inventory sources, enhance the output of Ansible commands, or modify the behavior of modules. Ansible includes a variety of built-in plugins, and users can also develop their own plugins to meet specific requirements.
Essential Components in Ansible
Out of the nodes above, there are the three most basic and essential elements needed to create a minimal Ansible automation workflow:
- A playbook to define the tasks and actions
- Modules to perform individual tasks
- An inventory to specify the target hosts
While other components like roles, plugins, filters, variables, handlers, and facts can enhance the functionality and flexibility of Ansible, they are not strictly necessary for a basic Ansible setup.
Playbook
A playbook in Ansible is a structured, ordered list of tasks written in YAML format. This ordered list of tasks can be executed repeatedly, ensuring consistent and reliable configuration management and deployment across the infrastructure. Playbooks can contain variables, tasks, and other constructs that enable complex configurations and orchestration.
Composition of Playbook
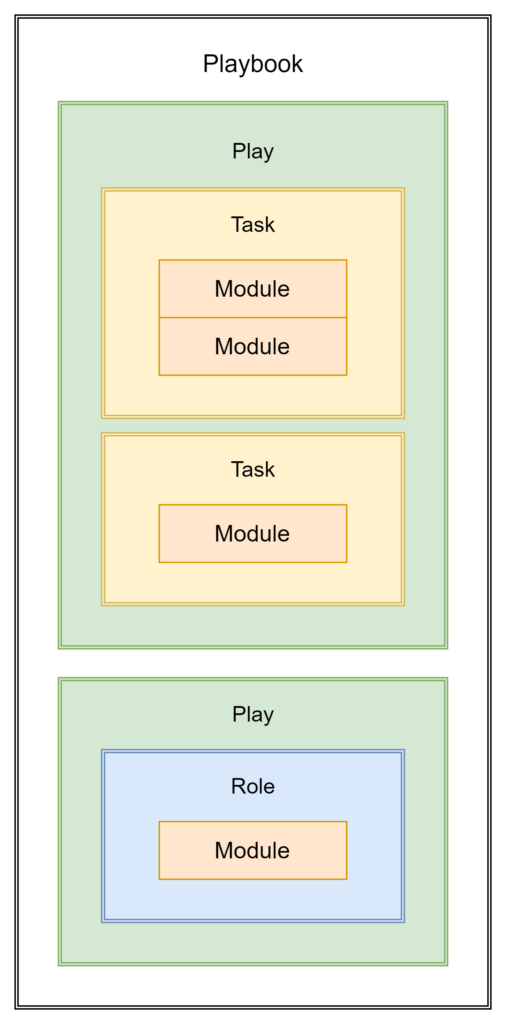
Playbooks are composed of one or more plays, which define the tasks to be executed on specific managed nodes. The composition of a playbook includes the following components:
- Plays: A play is a set of tasks executed on a group of managed nodes defined in the inventory. Each play targets a specific group of systems and contains tasks that are executed in the order they are defined. Plays provide a way to organize tasks based on the roles or functions of the targeted systems.
- Tasks: Tasks are the individual actions that make up a play. They represent the smallest unit of work in a playbook and are executed in the order they appear. Tasks utilize Ansible modules to perform specific actions, such as installing packages, configuring services, or managing files.
- Modules: Modules are the building blocks of tasks, providing the functionality needed to perform specific actions on managed nodes. Ansible includes a wide range of built-in modules, covering various aspects of system management and configuration. Users can also create custom modules to meet their unique requirements.
Example
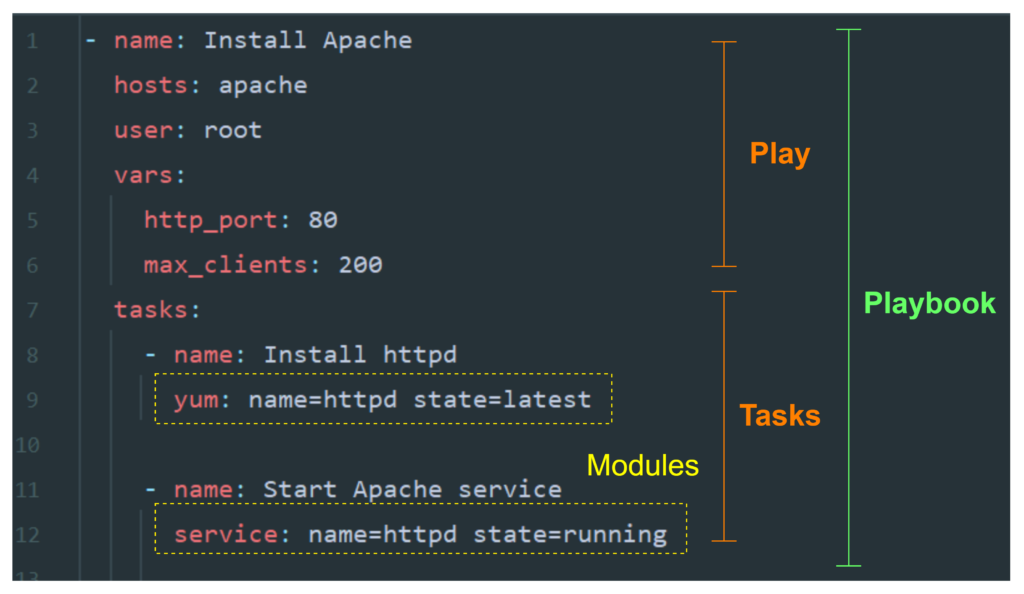
To better understand the concept of playbooks, plays, tasks, and modules, let’s examine a simple Ansible playbook example. In this example, we will install and start the Apache web server on a group of managed nodes:
- name: Install Apache
hosts: apache
user: root
vars:
http_port: 80
max_clients: 200
tasks:
- name: Install httpd
yum: name=httpd state=latest
- name: Start Apache service
service: name=httpd state=running
In this example, the playbook consists of a single play with the name “Install Apache”. The play targets the “apache” group of managed nodes, as specified by the “hosts” parameter. The “user” parameter indicates that the tasks will be executed as the root user.
The play defines two variables, “http_port” and “max_clients”, which can be used within the tasks to customize the Apache configuration. However, in this specific example, these variables are not used.
The play includes two tasks:
- “Install httpd”: This task utilizes the “yum” module to install the latest version of the “httpd” package (Apache web server) on the managed nodes. The “name” parameter specifies the package to install, while the “state” parameter indicates that the latest version should be installed.
- “Start Apache service”: This task uses the “service” module to ensure that the Apache service is started on the managed nodes. The “name” parameter specifies the service to manage, and the “state” parameter indicates that the service should be started.
In this example, the plays, tasks, and modules work together to install and start the Apache web server on the target group of managed nodes.
Module
A module in Ansible is a reusable, standalone script that performs a specific action on managed nodes. Modules are the foundation of tasks, providing the necessary functionality to automate various aspects of system management and configuration. They are essential for abstraction, reusability, and extensibility in Ansible. Ansible comes with a vast collection of built-in modules to address common use cases, and users can create custom modules to meet their unique requirements.
Types of Modules
Ansible modules can be categorized into several types, each designed to manage different aspects of the infrastructure. Some common types of modules include:
- Core Modules: These modules are maintained and supported by the Ansible core team. They cover a wide range of functionalities, such as package management, service control, file manipulation, and user administration.
- Network Modules: These modules are designed to manage network devices, such as switches, routers, and firewalls. They enable users to configure and manage network infrastructure using Ansible.
- Community Modules: Community modules are contributed and maintained by the Ansible community. They extend Ansible’s functionality to cover specialized use cases and third-party integrations.
- Custom Modules: Users can create custom modules to address specific needs that are not covered by built-in or community modules. Custom modules can be written in any programming language, as long as they can accept and return JSON data.
Example
let’s examine a simple example using the “copy” module, which is a core module for file management. This module is used to transfer files from the control node to managed nodes.
Here’s an example task that uses the “copy” module:
- name: Copy a file to managed nodes
copy:
src: /path/to/source/file.txt
dest: /path/to/destination/file.txt
owner: root
group: root
mode: '0644'
In this example, the “copy” module is used to transfer a file called “file.txt” from the control node to the managed nodes. The source file path is specified with the “src” parameter and the destination path on the managed nodes is specified with the “dest” parameter. The “owner”, “group”, and “mode” parameters are used to set the ownership and permissions for the file on the managed nodes.
This example demonstrates how modules provide the functionality needed to perform specific actions in tasks, enabling users to automate a wide range of system management and configuration tasks using Ansible.
Inventory
An inventory in Ansible is a list of managed nodes that are organized into groups, providing a way to target specific systems for configuration management and orchestration. The inventory is a crucial component of the Ansible architecture, as it defines the systems on which tasks will be executed. Inventories can be defined in various formats, such as static files, dynamic scripts, or even pulled from external sources like cloud providers and CMDBs.
Types of Inventory
- Static Inventory: A static inventory is a simple text file that lists managed nodes and organizes them into groups. This type of inventory is easy to create and maintain but might not be suitable for dynamic environments where systems are frequently added or removed.
- Dynamic Inventory: A dynamic inventory is a script or program that generates the list of managed nodes at runtime. This type of inventory is ideal for environments with a large number of systems or where systems are frequently added or removed. Dynamic inventories can be created using custom scripts or by leveraging Ansible’s built-in support for various cloud providers and other data sources.
Example
[web] webserver01.example.com webserver02.example.com [db] dbserver01.example.com [all:vars] ansible_user=myuser ansible_ssh_private_key_file=/path/to/private/key.pem
This example demonstrates how inventories organize managed nodes into groups and define variables for Ansible tasks, enabling users to target specific systems and apply consistent configurations across their infrastructure.
the inventory file defines two groups: “web” and “db”. The “web” group contains two managed nodes, “webserver01.example.com” and “webserver02.example.com”, while the “db” group contains a single managed node, “dbserver01.example.com”.
Group variables are defined under the “all:vars” section, which applies to all managed nodes in the inventory. In this case, the “ansible_user” variable specifies the user for SSH connections, and the “ansible_ssh_private_key_file” variable specifies the path to the private key for authentication.
Conclusion
Through an examination of Ansible’s architecture, we explored essential components such as playbooks, modules, and inventory, highlighting their roles in automating tasks and managing configurations across various systems. The examples provided throughout the article serve to demonstrate the flexibility and power of Ansible as a tool for managing complex, multi-tier infrastructures.
In summary, Ansible is an invaluable tool for IT professionals seeking to automate infrastructure management, application deployment, and configuration tasks. Its simplicity, power, and flexibility make it a popular choice across numerous industries and organizations. By learning and mastering Ansible, you can significantly streamline your infrastructure management and deployment processes, ensuring consistency, reliability, and efficiency in your IT environment.
